Introduction
In today’s hyperconnected world, cybersecurity is no longer just a backend concern—it’s a frontline feature of user experience. As digital threats grow more sophisticated, users demand more than functionality and aesthetics; they want trust. That trust must be embedded into every pixel, every interaction, and every line of code. Let’s see Cybersecurity by Design: Building Trust into Every Pixel.
Cybersecurity by design is a proactive approach to building secure digital products from the ground up. It’s about integrating security into the DNA of your app or website—not as an afterthought, but as a core design principle.
This blog explores the concept of cybersecurity by design, its importance, key principles, implementation strategies, and how it enhances user trust and brand reputation.
What Is Cybersecurity by Design?
Cybersecurity by design is the practice of embedding security measures into the architecture, interface, and user experience of digital products from the earliest stages of development.
Key Goals:
- Prevent vulnerabilities before they occur
- Protect user data and privacy
- Ensure secure interactions
- Build user confidence and trust
Why Cybersecurity Must Be a Design Priority
🔐 Rising Threat Landscape
Cyberattacks are more frequent and damaging than ever—ransomware, phishing, data breaches, and zero-day exploits affect businesses of all sizes.
🧠 User Awareness
Users are increasingly savvy about digital risks. They expect secure logins, encrypted communications, and transparent data practices.
📜 Regulatory Compliance
Laws like GDPR, CCPA, and India’s DPDP Act mandate secure data handling and user consent.
💬 Brand Reputation
Security breaches can destroy trust and lead to customer churn, legal penalties, and PR disasters.
Core Principles of Cybersecurity by Design
1. Privacy by Design
- Minimize data collection
- Use anonymization and pseudonymization
- Provide granular user controls
2. Least Privilege
- Limit access to only what’s necessary
- Use role-based permissions
3. Secure Defaults
- Enable security features by default (e.g., HTTPS, MFA)
4. Defense in Depth
- Layered security: firewalls, encryption, authentication, monitoring
5. Fail-Safe Design
- Ensure systems degrade gracefully under attack or failure
6. Transparency
- Inform users about data usage, security measures, and breaches
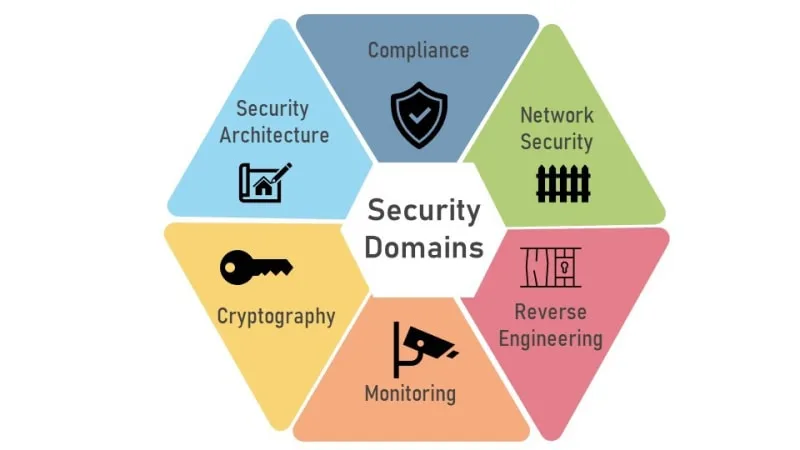
Designing Secure Interfaces
🧭 Secure Navigation
- Use HTTPS everywhere
- Validate URLs and prevent redirects
🔐 Authentication UX
- Support multi-factor authentication (MFA)
- Use biometric options where appropriate
- Avoid password fatigue with secure alternatives
🧾 Form Security
- Validate inputs client-side and server-side
- Use CAPTCHA and bot detection
- Prevent injection attacks
🧠 Feedback and Alerts
- Notify users of suspicious activity
- Provide clear error messages without revealing system details
🧩 Session Management
- Auto-logout after inactivity
- Use secure cookies and tokens
Front-End Security Techniques
✅ Content Security Policy (CSP)
Prevents cross-site scripting (XSS) by restricting resource loading.
✅ Subresource Integrity (SRI)
Ensures third-party scripts haven’t been tampered with.
✅ Cross-Origin Resource Sharing (CORS)
Controls which domains can access your resources.
✅ Secure Headers
Use HTTP headers like X-Frame-Options, Strict-Transport-Security, and X-Content-Type-Options.
✅ Input Sanitization
Clean user inputs to prevent injection attacks.
Embedding Security in the Development Lifecycle
1. Planning Phase
- Conduct threat modeling
- Define security requirements
2. Design Phase
- Choose secure frameworks and libraries
- Design for data minimization
3. Development Phase
- Use secure coding practices
- Perform static code analysis
4. Testing Phase
- Conduct penetration testing
- Use automated vulnerability scanners
5. Deployment Phase
- Secure CI/CD pipelines
- Monitor for anomalies
6. Maintenance Phase
- Patch vulnerabilities promptly
- Audit logs and access regularly
Tools for Cybersecurity by Design
- OWASP ZAP – Vulnerability scanner
- Burp Suite – Web security testing
- SonarQube – Code quality and security analysis
- Snyk – Open-source dependency scanning
- Auth0 / Firebase Auth – Secure authentication platforms
Case Studies
🛒 Shopify
Implements security at every layer—from secure APIs to user-friendly MFA—earning trust from millions of merchants.
📱 Signal
Built with end-to-end encryption and zero data retention, Signal exemplifies privacy-first design.
🧠 Duolingo
Uses secure session management and input validation to protect user data while maintaining a playful UX.

Balancing Security and Usability
Security should never feel like a burden. The best designs make secure behavior the default, not the exception.
🧠 Tips:
- Use biometric authentication for ease and safety
- Offer passwordless login options
- Provide clear feedback on security actions (e.g., “Your data is encrypted”)
Common Pitfalls to Avoid
❌ Hardcoded Credentials
Never store passwords or API keys in code.
❌ Overly Complex Security
Don’t make users jump through hoops—balance protection with convenience.
❌ Ignoring Mobile Security
Mobile apps are often less protected than web apps. Apply the same rigor.
❌ Neglecting Third-Party Risks
Vet all plugins, libraries, and APIs for vulnerabilities.
Future Trends in Secure Design
1. AI-Powered Threat Detection
Real-time anomaly detection using machine learning.
2. Privacy-Enhancing Technologies (PETs)
Techniques like differential privacy and homomorphic encryption.
3. Zero Trust Architecture
Assumes no user or device is inherently trustworthy—verifies everything.
4. Secure-by-Default Frameworks
Development platforms that enforce security best practices automatically.
Conclusion
Cybersecurity by design is not just a technical strategy—it’s a commitment to building trust. In a digital world where every pixel matters, secure design ensures that users feel safe, respected, and empowered. By embedding security into every layer of development, businesses can protect their users, their reputation, and their future.
The best security is invisible—but always present. It’s not just about defending against threats; it’s about designing with integrity.