Introduction
WordPress powers over 40% of all websites on the internet, making it a prime target for hackers and malicious bots. While its popularity stems from flexibility and ease of use, it also means that vulnerabilities—if left unaddressed—Securing Your WordPress Site.
For developers, securing a WordPress site goes beyond installing a few plugins. It requires a layered approach that includes server hardening, code hygiene, access control, and ongoing monitoring. In this blog, we’ll explore the most effective security practices for developers to safeguard WordPress sites from threats.
1. Keep WordPress Core, Themes, and Plugins Updated
Why It Matters
Outdated software is one of the most common entry points for attackers. Updates often include patches for known vulnerabilities.
Best Practices
- Enable automatic updates for minor releases.
- Regularly check for updates to themes and plugins.
- Remove unused themes and plugins to reduce attack surface.
- Subscribe to vulnerability databases like WPScan for alerts.
2. Use Trusted Themes and Plugins
Why It Matters
Poorly coded or malicious plugins can introduce vulnerabilities.
Best Practices
- Download only from the official WordPress repository or reputable developers.
- Review plugin ratings, update history, and support activity.
- Audit plugin code if using custom or third-party sources.
- Limit the number of plugins to reduce complexity and risk.
3. Implement Strong Authentication
Why It Matters
Weak passwords and default usernames are easy targets for brute-force attacks.
Best Practices
- Enforce strong password policies using plugins like iThemes Security.
- Change the default “admin” username.
- Use two-factor authentication (2FA) for all admin accounts.
- Limit login attempts and use CAPTCHA to deter bots.
4. Secure wp-config.php and .htaccess Files
Why It Matters
These files contain sensitive configuration data and control access rules.
Best Practices
- Move
wp-config.phpone directory above the root if possible. - Set file permissions to
400or440. - Use
.htaccessto block access:
<Files wp-config.php>
order allow,deny
deny from all
</Files>
- Disable directory browsing:
Options -Indexes

5. Use HTTPS and SSL Certificates
Why It Matters
SSL encrypts data between the user and server, protecting login credentials and personal information.
Best Practices
- Install an SSL certificate via your hosting provider or Let’s Encrypt.
- Force HTTPS using plugins or
.htaccessrules. - Update WordPress and site URLs to use
https://.
6. Harden File Permissions
Why It Matters
Incorrect file permissions can allow unauthorized access or modification.
Recommended Settings
- Files:
644 - Directories:
755 - wp-config.php:
400or440
Best Practices
- Avoid
777permissions at all costs. - Use SSH or SFTP to manage permissions securely.
- Regularly audit file permissions for anomalies.
7. Disable XML-RPC if Not Needed
Why It Matters
XML-RPC is often exploited for brute-force and DDoS attacks.
Best Practices
- Disable XML-RPC using plugins like Disable XML-RPC.
- Alternatively, block access via
.htaccess:
<Files xmlrpc.php>
order deny,allow
deny from all
</Files>
- If needed for Jetpack or mobile apps, restrict access with authentication.
8. Limit Admin Access and User Roles
Why It Matters
Overprivileged accounts increase the risk of accidental or malicious changes.
Best Practices
- Assign the minimum required role (Editor, Author, Contributor).
- Use custom roles for granular control.
- Audit user accounts regularly and remove inactive users.
- Log user activity for accountability.
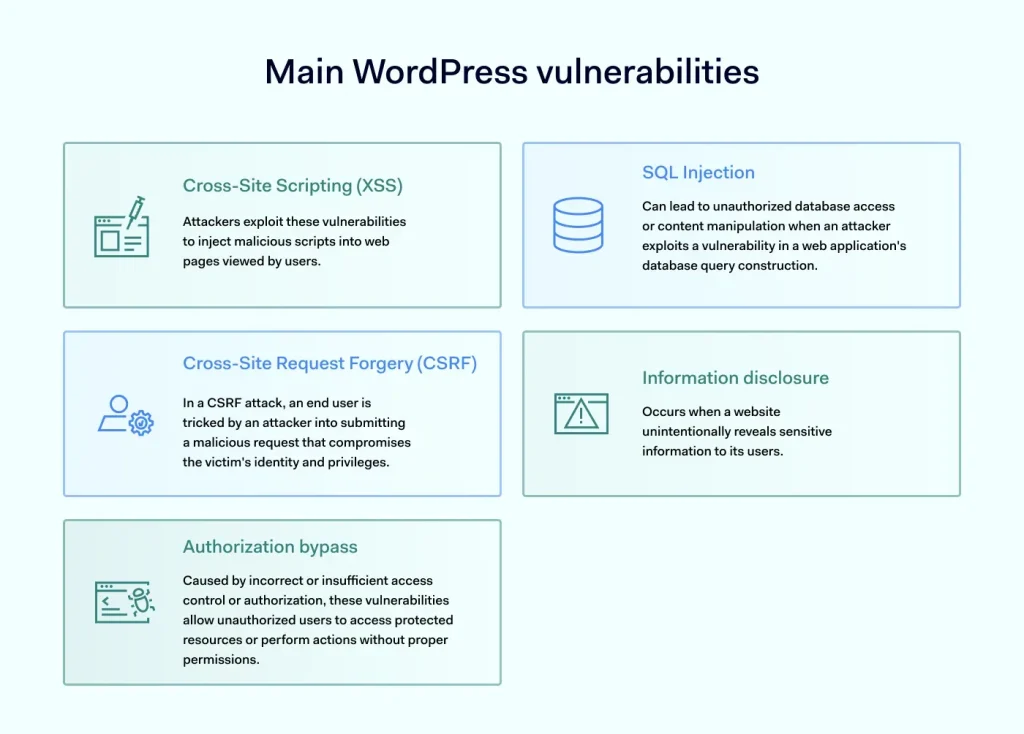
9. Protect Against SQL Injection and XSS
Why It Matters
SQL injection and cross-site scripting (XSS) are common attack vectors.
Best Practices
- Use WordPress functions like
prepare()for database queries. - Sanitize and escape all user inputs using
sanitize_text_field(),esc_html(), etc. - Validate form data on both client and server sides.
- Use security plugins that scan for vulnerabilities.
10. Monitor and Log Activity
Why It Matters
Real-time monitoring helps detect and respond to threats quickly.
Best Practices
- Use plugins like WP Activity Log or Sucuri Security.
- Monitor login attempts, file changes, and plugin installations.
- Set up alerts for suspicious activity.
- Store logs securely and review them regularly.
11. Backup Regularly and Automate It
Why It Matters
Backups are your safety net in case of hacks, data loss, or server failure.
Best Practices
- Use plugins like UpdraftPlus, BlogVault, or Jetpack Backup.
- Schedule automatic backups daily or weekly.
- Store backups offsite (e.g., Dropbox, Google Drive, Amazon S3).
- Test backup restoration periodically.
12. Use a Web Application Firewall (WAF)
Why It Matters
A WAF filters malicious traffic before it reaches your site.
Best Practices
- Use services like Cloudflare, Sucuri, or Wordfence.
- Block known bad IPs and bots.
- Enable rate limiting and DDoS protection.
- Monitor firewall logs for threats.
13. Secure the Database
Why It Matters
The database stores all site content and user data.
Best Practices
- Change the default
wp_table prefix. - Use strong database credentials.
- Restrict database access to localhost.
- Regularly optimize and clean the database.
14. Hide WordPress Version
Why It Matters
Exposing your WordPress version helps attackers target known vulnerabilities.
Best Practices
- Remove version meta tag from header:
remove_action('wp_head', 'wp_generator');
- Use security plugins to hide version info.
- Keep WordPress updated to reduce risk.

15. Scan for Malware and Vulnerabilities
Why It Matters
Malware can go undetected and cause long-term damage.
Best Practices
- Use plugins like Wordfence, Sucuri, or MalCare.
- Schedule regular scans.
- Quarantine or delete infected files.
- Monitor for blacklisting or spam flags.
16. Secure Hosting Environment
Why It Matters
Your hosting provider plays a major role in site security.
Best Practices
- Choose hosts with built-in security features (firewalls, malware scanning).
- Use managed WordPress hosting for automatic updates and backups.
- Enable server-level caching and isolation.
- Keep PHP and MySQL versions up to date.
17. Educate Clients and Team Members
Why It Matters
Security is a shared responsibility.
Best Practices
- Train users on password hygiene and phishing awareness.
- Limit access to sensitive areas.
- Create documentation for security protocols.
- Encourage regular audits and updates.
Conclusion
Securing a WordPress site is an ongoing process—not a one-time task. Developers must adopt a proactive, layered approach that combines secure coding practices, server hardening, user management, and real-time monitoring. By following these best practices, you can protect your site from common threats and ensure a safe experience for users and clients.
Whether you’re building a blog, e-commerce store, or enterprise portal, security should be baked into every stage of development. Stay informed, stay vigilant, and keep your WordPress site secure.





